Post 1: Display Filtering in Wireshark
November 29, 2018 at | In Network Forensics | No CommentsWireshark is an open source graphic user interface (GUI) that can be used to examine and analyze network packets. It can understand different networking protocols, such as TCP, UDP, and HTTP. Wireshark intercepts traffic in binary form and convert the binary form into a readable form, which makes it easier to identify what traffic is crossing the network. Unlike the other packet analyzer such as tcpdump, Wireshark makes filtering easier, using certain commands.
In this post, I will explain some of the simple and most-used commands to filter a packet. Before starting, the first thing you need to do is open a pcap file and open it on Wireshark.
Display filter based on protocol type
To filter results based on the protocol type, type the protocol name that you wanted to see. For example, if you want to see only the TCP protocol of the pcap file, just type tcp on the search bar, and all the packages with the TCP protocol will appear.
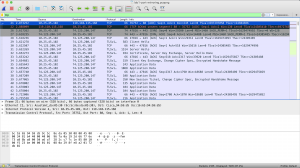
If you need to see more than 1 different protocols, use the command protocol1 || protocol2. The || represents the logical OR separator. For example, you need information for 3 different protocols, which consists of http, tcp, and arp. So you need to use the command http || tcp || arp, and it will show you the informations based on that 3 protocols.
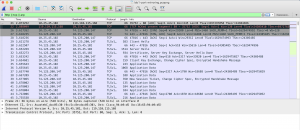
Display filter based on port number
To filter the results based on a certain TCP port number, use the command tcp.port == PortNumber. If you want to filter based on 2 TCP port numbers, use the command (tcp.port == PortNumber) or (tcp.port == PortNumber). In the example, I am going to filter TCP ports 80, so I am going to use the command tcp.port ==80, and the result is shown below, where only the TCP with port 80 is shown.
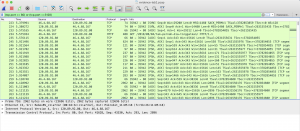
For UDP port, similar to TCP, use the command udp.port == PortNumber to only show one port only. To filter both TCP and UDP ports, use the command tcp.port == PortNumber || udp.port == PortNumber.
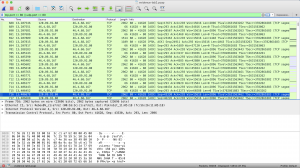
Display filter based on IP address
To filter the results based on the IP source, use the command ip.src == IPAddress. The example can be shown in the picture below, where I want to show the result based on IP address 10.25.45.102, so I use the command ip.src == 10.25.45.102.
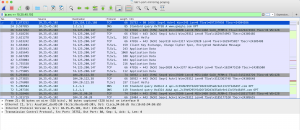
To filter it based on the IP destination, use the command ip.dst == IPAddress. If you want to filter the results based on both the source and destination, use the command ip.addr == IPAddress.
If you want to exclude the packets with a certain IP address, use the command ip.src != IPAddress.
To see other display filters for Wireshark, check out these useful websites below where they explain more filtering commands that can be useful to analyze pcap files using Wireshark.
Source:
- https://wiki.wireshark.org/DisplayFilters
- https://www.maketecheasier.com/use-display-filters-in-wireshark/
Powered by WordPress with Pool theme design by Borja Fernandez.
Entries and comments feeds.
Valid XHTML and CSS. ^Top^