Post 9: Centralized Logs
January 8, 2019 at | In Network Forensics | No CommentsCentralized logs is where we can see the activity of a virtual machine in another virtual machine. To try centralized logs, it is important to have one virtual machine that will act as the log server, and a second virtual machine. In this tutorial, I will use kali linux as the OS for both virtual machines. Then set the connection of both virtual machines into bridged adapter by selecting the virtual machine from the VirtualBox application, then go to network, and select the Bridged Adapter option. Do the same to the second virtual machine.
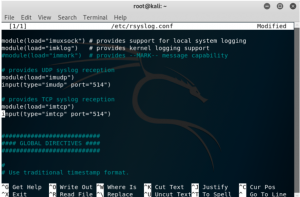
Start the first virtual machine that will be the log server, then open its terminal. Edit the file /etc/rsyslog.conf using the command “nano cat /etc/rsyslog.conf”, and uncomment the lines that provides the UDP and TCP syslog reception, by erasing the #. Imudp stands for input module UDP, and imtcp stands for input module TCP. Enabling the two modules will open port 514 from both UDP and TCP for incoming log data from other virtual machines.
After finish editing the modules, save the file and use the command “service rsyslog restart” to restart syslog. Now check if the port 514 from UDP and TCP has been open using the “netstat -pln | grep 514” command, and it will show just like the screenshot below if it’s been opened. 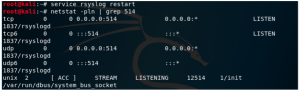
Check the first virtual machine’s IP address using if config. Make sure that the first and second virtual machines’s IP address is not the same or else centralized log will not work.
Open the second virtual machine that will act as the client. Open it’s terminal, and create file in etc/rsyslog.d/test.conf using the command vim /etc/rsyslog.d/test.conf. A blank page will appear in the terminal, then press “i” to write. In the file, write “*.* @Log server IP address”. To save the file, press the “esc” button first on the keyboard, then write “:wq” to save and quit the editor.

To check the configuration, type cat /etc/rsyslog.d/test.conf, and the result shown will be the same entry that is written in the test.conf file in the previous step. ![]()
Go back to the log server to monitor the log, and use the command tail -f /var/log/syslog /var/log/auth.log. This will show that the current log will only come from the VM as the log machine. 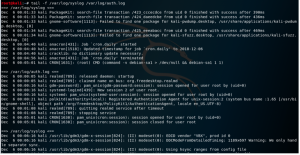
Then go back to the second VM, which is the client, and type service rsyslog restart. Go back to the first VM, and check that the name of the other VM is shown in the log server, as shown in the screenshot below. 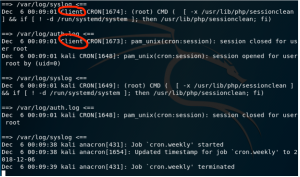
No Comments yet »
RSS feed for comments on this post. TrackBack URI
Leave a comment
Powered by WordPress with Pool theme design by Borja Fernandez.
Entries and comments feeds.
Valid XHTML and CSS. ^Top^