Post 3: Recreate a Website from a Pcap Capture
January 8, 2019 at | In Network Forensics | No CommentsRecreating a website to see what the website looks like using pcap capture is possible, by first finding the packet that has HTTP protocol. Filter the packet to only show HTTP by using the command ‘http’.

Find the packet that has a website on it, by looking at the info, and right click then select follow TCP stream.

A new window will pop and show the HTML code of the selected website, as shown below.

Change the data into raw data by selecting ‘Raw’ from the show and save data on the bottom part of the window, then save it by clicking ‘save as’.
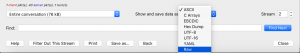
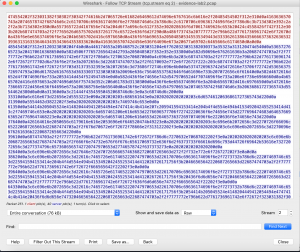
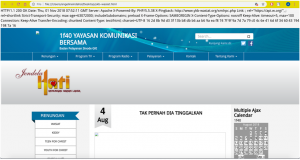
Go to the location of the saved file and open it in a browser, and you will see that the website has been successfully created.
Post 2: Common Ports and Protocols
January 2, 2019 at | In Network Forensics | No CommentsIn programming, a port is a way for the client program to specifically specify certain programs on a computer in a network, using TCP/IP. Ports have assigned numbers that have been assigned by the Internet Assigned Numbers Authority, or IANA. When a server starts, it will automatically bind to the assigned port number. Port numbers range from number 0 to 65535. Well-known ports starts from port number 1 until port number 1024. Well-known ports are for communication from the application endpoints to the TCP and UDP of the internet. In network forensics, well-known ports are very important to identify what protocol is used in the network traffic, and to analyze if the protocol had vulnerabilities in it.
Here are the list of well-known ports that should be memorized by investigators.
20(UDP) = FTP data
21(TCP/UDP) = FTP
22 = SSH
23(TCP) = Telnet
25(TCP) = SMTP
80(TCP) =HTTP
110(TCP) = POP3
143(TCP) = IMAP
443(TCP) = HTTPS
389(TCP) = LOAD
3306(TCP) = MYSQL
5432(TCP) = PostgreSQL
995(TCP) = IMAPS
993(TCP) = POP3S
564(TCP) = SMPT over SSL
587(TCP) = SMTP over TLS
123(UDP) = NTP
113(TCP) = DENTD
69(UDP) = TFTP
3128(TCP) = HTTP proxy
8080(TCP) = HTTP proxy
3389(TCP) = Remote desktop
5901(TCP) = VMC
6660-7002(TCP) = IRC
Source:
- https://searchnetworking.techtarget.com/definition/well-known-port-numbers
Post 1: Display Filtering in Wireshark
November 29, 2018 at | In Network Forensics | No CommentsWireshark is an open source graphic user interface (GUI) that can be used to examine and analyze network packets. It can understand different networking protocols, such as TCP, UDP, and HTTP. Wireshark intercepts traffic in binary form and convert the binary form into a readable form, which makes it easier to identify what traffic is crossing the network. Unlike the other packet analyzer such as tcpdump, Wireshark makes filtering easier, using certain commands.
In this post, I will explain some of the simple and most-used commands to filter a packet. Before starting, the first thing you need to do is open a pcap file and open it on Wireshark.
Display filter based on protocol type
To filter results based on the protocol type, type the protocol name that you wanted to see. For example, if you want to see only the TCP protocol of the pcap file, just type tcp on the search bar, and all the packages with the TCP protocol will appear.
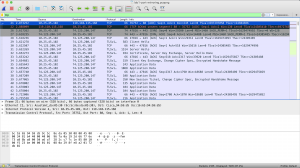
If you need to see more than 1 different protocols, use the command protocol1 || protocol2. The || represents the logical OR separator. For example, you need information for 3 different protocols, which consists of http, tcp, and arp. So you need to use the command http || tcp || arp, and it will show you the informations based on that 3 protocols.
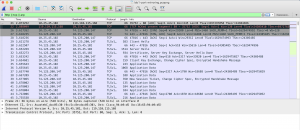
Display filter based on port number
To filter the results based on a certain TCP port number, use the command tcp.port == PortNumber. If you want to filter based on 2 TCP port numbers, use the command (tcp.port == PortNumber) or (tcp.port == PortNumber). In the example, I am going to filter TCP ports 80, so I am going to use the command tcp.port ==80, and the result is shown below, where only the TCP with port 80 is shown.
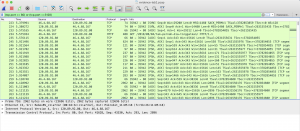
For UDP port, similar to TCP, use the command udp.port == PortNumber to only show one port only. To filter both TCP and UDP ports, use the command tcp.port == PortNumber || udp.port == PortNumber.
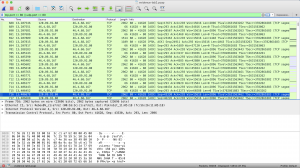
Display filter based on IP address
To filter the results based on the IP source, use the command ip.src == IPAddress. The example can be shown in the picture below, where I want to show the result based on IP address 10.25.45.102, so I use the command ip.src == 10.25.45.102.
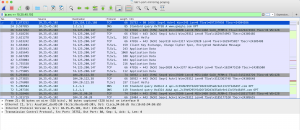
To filter it based on the IP destination, use the command ip.dst == IPAddress. If you want to filter the results based on both the source and destination, use the command ip.addr == IPAddress.
If you want to exclude the packets with a certain IP address, use the command ip.src != IPAddress.
To see other display filters for Wireshark, check out these useful websites below where they explain more filtering commands that can be useful to analyze pcap files using Wireshark.
Source:
- https://wiki.wireshark.org/DisplayFilters
- https://www.maketecheasier.com/use-display-filters-in-wireshark/
Powered by WordPress with Pool theme design by Borja Fernandez.
Entries and comments feeds.
Valid XHTML and CSS. ^Top^